Covertix's SmartCipher
Covertix's SmartCipher is a file-level, rights-management system that monitors and secures sensitive data, inside and outside the organization. The system automatically classifies digital assets according to their location, content and/or context, and continuously tracks and secures these assets. It protects documents even when the user is offline, as usage policies are encrypted within the file and a connection with the server is not required. SmartCipher offers real time control and enables restriction of certain actions on files and real-time alerts each time usage policies are violated.
System Components
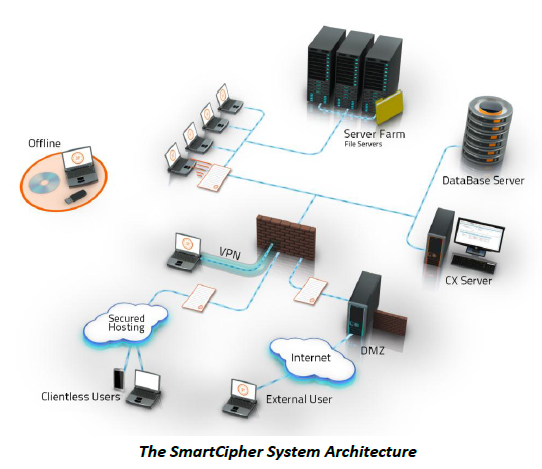
The following block diagram provides an overview of the SmartCipher system components and configuration. A management server, comprising an IIS server and a DB server, is used to manage and administer the system. It communicates with the SmartCipher client - an end-point host component which identifies files to be protected and enforces usage policies for protected files. Communication and control of files outside the corporate network, is achieved using a DMZ server outside the Firewall. The server is not required for the system to work. Policies travel with the files and are enforced and executed by the end-point client.
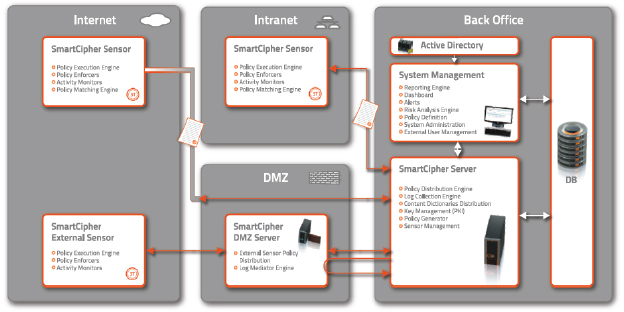
SmartCipher Server
The SmartCipher Server manages communications with all clients installed on end-user devices via "smart policies". The "smart policies" includes the following modules which communicate with the clients:
- Policy Distribution Engine: Distributes policies to all clients – wherever a "smart policy" is installed.
- Log Collection Engine: Receives all reports and alerts containing policy infractions received from clients and forwards the information to the database.
- Content Dictionaries Distribution: Distributes dictionaries and sends updated dictionaries to all clients.
- Key Management (PKI): Distributes digital management keys to clients.
- Policy Generator: Creates "smart policies" which are distributed by the Policy Distribution Engine to each client.
- Client Management: Manages the clients and ensures they are functioning properly.
Peripheral Server
The SmartCipher DMZ Server is a mediator between the SmartCipher Server and external clients. All policy rules are automatically maintained.
SmartCipher Client
The SmartCipher Client, installed on all internal and external devices, comprises:
- Policy Execution Engine: When a file is opened, its "smart policy" uses this engine to apply appropriate policy rules.
- Policy Enforcers: Ensures that rules making up a policy are enforced in the relevant files.
- Activity Monitoring: Reports on user activities according to Policy Execution Engine directives.
- Policy Matching Engine: Matches the appropriate policy to files based on the business rules defined centrally in the management server.
SmartCipher External Client
The SmartCipher External Client is applied to third-party users and enforces policy matching on files that are transmitted beyond the corporate firewall. A rule can specify that access to a document located beyond the firewall is blocked or limited, even on a laptop which belongs to the organization.
Clientless User
SmartCipher also offers a solution for users without the SmartCipher client. In this procedure the sensitive file is uploaded to a secured server and the user receives a unique web link which allows him to view the document on a web browser. The link can be password protected and limited privileges can be granted to the user. This solution is suitable for secured file sharing with occasional third-party users or internal users traveling with smartphones.
External User Management
SmartCipher works in a similar manner for both internal and external users. External users register for single access and SmartCipher automatically generates personalized encryption keys for authentication purposes. The whole process is transparent to the end-user. When an external, authorized user receives a SmartCipher encrypted file, the user's client automatically decrypts the file and the embedded usage policy governs its use. Needless to say, if the user is not authorized to deal with the file or does not have the client installed, the document will not open.

